 |
| June 12, 2018 | Volume 14 Issue 22 |
Mechanical News & Products
Designfax weekly eMagazine
Archives
Partners
Manufacturing Center
Product Spotlight
Modern Applications News
Metalworking Ideas For
Today's Job Shops
Tooling and Production
Strategies for large
metalworking plants
hyperMILL 2024 CAD/CAM software suite
 OPEN MIND Technologies has introduced its latest hyperMILL 2024 CAD/CAM software suite, which includes a range of powerful enhancements to its core toolpath capabilities, as well as new functionality for increased NC programming efficiency in applications ranging from 2.5D machining to 5-axis milling. New and enhanced capabilities include: Optimized Deep Hole Drilling, a new algorithm for 3- and 5-axis Rest Machining, an enhanced path layout for the 3D Plane Machining cycle, better error detection, and much more.
OPEN MIND Technologies has introduced its latest hyperMILL 2024 CAD/CAM software suite, which includes a range of powerful enhancements to its core toolpath capabilities, as well as new functionality for increased NC programming efficiency in applications ranging from 2.5D machining to 5-axis milling. New and enhanced capabilities include: Optimized Deep Hole Drilling, a new algorithm for 3- and 5-axis Rest Machining, an enhanced path layout for the 3D Plane Machining cycle, better error detection, and much more.
Learn more.
One-part epoxy changes from red to clear under UV
 Master Bond UV15RCL is a low-viscosity, cationic-type UV-curing system with a special color-changing feature. The red material changes to clear once exposed to UV light, indicating that there is UV light access across the adhesive material. Although this change in color from red to clear does not indicate a full cure, it does confirm that the UV light has reached the polymer. This epoxy is an excellent electrical insulator. UV15RCL adheres well to metals, glass, ceramics, and many plastics, including acrylics and polycarbonates.
Master Bond UV15RCL is a low-viscosity, cationic-type UV-curing system with a special color-changing feature. The red material changes to clear once exposed to UV light, indicating that there is UV light access across the adhesive material. Although this change in color from red to clear does not indicate a full cure, it does confirm that the UV light has reached the polymer. This epoxy is an excellent electrical insulator. UV15RCL adheres well to metals, glass, ceramics, and many plastics, including acrylics and polycarbonates.
Learn more.
SPIROL Press-N-Lok™ Pin for plastic housings
 The Press-N-Lok™ Pin was designed to permanently retain two plastic components to each other. As the pin is inserted, the plastic backfills into the area around the two opposing barbs, resulting in maximum retention. Assembly time is quicker, and it requires lower assembly equipment costs compared to screws and adhesives -- just Press-N-Lok™!
The Press-N-Lok™ Pin was designed to permanently retain two plastic components to each other. As the pin is inserted, the plastic backfills into the area around the two opposing barbs, resulting in maximum retention. Assembly time is quicker, and it requires lower assembly equipment costs compared to screws and adhesives -- just Press-N-Lok™!
Learn more about the new Press-N-Lok™ Pin.
Why hybrid bearings are becoming the new industry standard
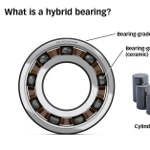 A combination of steel outer and inner rings with ceramic balls or rollers is giving hybrid bearings unique properties, making them suitable for use in a wide range of modern applications. SKF hybrid bearings make use of silicon nitride (twice as hard as bearing steel) rolling elements and are available as ball bearings, cylindrical roller bearings, and in custom designs. From electric erosion prevention to friction reduction and extended maintenance intervals, learn all about next-gen hybrid bearings.
A combination of steel outer and inner rings with ceramic balls or rollers is giving hybrid bearings unique properties, making them suitable for use in a wide range of modern applications. SKF hybrid bearings make use of silicon nitride (twice as hard as bearing steel) rolling elements and are available as ball bearings, cylindrical roller bearings, and in custom designs. From electric erosion prevention to friction reduction and extended maintenance intervals, learn all about next-gen hybrid bearings.
Read the SKF technical article.
3M and Ansys train engineers on simulating adhesives
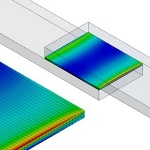 Ansys and 3M have created an advanced simulation training program enabling engineers to enhance the design and sustainability of their products when using tapes and adhesives as part of the design. Simulation enables engineers to validate engineering decisions when analyzing advanced polymeric materials -- especially when bonding components made of different materials. Understand the behavior of adhesives under real-world conditions for accurate modeling and design.
Ansys and 3M have created an advanced simulation training program enabling engineers to enhance the design and sustainability of their products when using tapes and adhesives as part of the design. Simulation enables engineers to validate engineering decisions when analyzing advanced polymeric materials -- especially when bonding components made of different materials. Understand the behavior of adhesives under real-world conditions for accurate modeling and design.
Read this informative Ansys blog.
New FATH T-slotted rail components in black from AutomationDirect
 Automation-Direct has added a wide assortment of black-colored FATH T-slotted hardware components to match their SureFrame black anodized T-slotted rails, including: cube connectors (2D and 3D) and angle connectors, joining plates of many types, brackets, and pivot joints. Also included are foot consoles, linear bearings in silver and black, cam lever brakes, and L-handle brakes. FATH T-slotted hardware components are easy to install, allow for numerous T-slotted structure configurations, and have a 1-year warranty against defects.
Automation-Direct has added a wide assortment of black-colored FATH T-slotted hardware components to match their SureFrame black anodized T-slotted rails, including: cube connectors (2D and 3D) and angle connectors, joining plates of many types, brackets, and pivot joints. Also included are foot consoles, linear bearings in silver and black, cam lever brakes, and L-handle brakes. FATH T-slotted hardware components are easy to install, allow for numerous T-slotted structure configurations, and have a 1-year warranty against defects.
Learn more.
Weird stuff: Moon dust simulant for 3D printing
 Crafted from a lunar regolith simulant, Basalt Moon Dust Filamet™ (not a typo) available from The Virtual Foundry closely mirrors the makeup of lunar regolith found in mare regions of the Moon. It enables users with standard fused filament fabrication (FFF) 3D printers to print with unparalleled realism. Try out your ideas before you go for that big space contract, or help your kid get an A on that special science project.
Crafted from a lunar regolith simulant, Basalt Moon Dust Filamet™ (not a typo) available from The Virtual Foundry closely mirrors the makeup of lunar regolith found in mare regions of the Moon. It enables users with standard fused filament fabrication (FFF) 3D printers to print with unparalleled realism. Try out your ideas before you go for that big space contract, or help your kid get an A on that special science project.
Learn more.
Break the mold with custom injection molding by Rogan
 With 90 years of industry experience, Rogan Corporation possesses the expertise to deliver custom injection molding solutions that set businesses apart. As a low-cost, high-volume solution, injection molding is the most widely used plastics manufacturing process. Rogan processes include single-shot, two-shot, overmolding, and assembly. Elevate your parts with secondary operations: drilling and tapping, hot stamping, special finishes, punch press, gluing, painting, and more.
With 90 years of industry experience, Rogan Corporation possesses the expertise to deliver custom injection molding solutions that set businesses apart. As a low-cost, high-volume solution, injection molding is the most widely used plastics manufacturing process. Rogan processes include single-shot, two-shot, overmolding, and assembly. Elevate your parts with secondary operations: drilling and tapping, hot stamping, special finishes, punch press, gluing, painting, and more.
Learn more.
World's first current-carrying fastening technology
 PEM® eConnect™ current-carrying pins from Penn-Engineering provide superior electrical connections in applications that demand high performance from internal components, such as automotive electronics. This first-to-market tech provides repeatable, consistent electrical joints and superior installation unmatched by traditional fastening methods. Features include quick and secure automated installation, no hot spots or poor conductivity, and captivation options that include self-clinching and broaching styles.
PEM® eConnect™ current-carrying pins from Penn-Engineering provide superior electrical connections in applications that demand high performance from internal components, such as automotive electronics. This first-to-market tech provides repeatable, consistent electrical joints and superior installation unmatched by traditional fastening methods. Features include quick and secure automated installation, no hot spots or poor conductivity, and captivation options that include self-clinching and broaching styles.
Learn more about eConnect pins.
New interactive digital catalog from EXAIR
 EXAIR's latest catalog offers readers an incredible source of innovative solutions for common industrial problems like conveying, cooling, cleaning, blowoff, drying, coating, and static buildup. This fully digital and interactive version of Catalog 35 is designed for easy browsing and added accessibility. Customers can view, download, print, and save either the full catalog or specific pages and sections. EXAIR products are designed to conserve compressed air and increase personnel safety in the process. Loaded with useful information.
EXAIR's latest catalog offers readers an incredible source of innovative solutions for common industrial problems like conveying, cooling, cleaning, blowoff, drying, coating, and static buildup. This fully digital and interactive version of Catalog 35 is designed for easy browsing and added accessibility. Customers can view, download, print, and save either the full catalog or specific pages and sections. EXAIR products are designed to conserve compressed air and increase personnel safety in the process. Loaded with useful information.
Check out EXAIR's online catalog.
5 cost-saving design tips for CNC machining
 Make sure your parts meet expectations the first time around. Xometry's director of application engineering, Greg Paulsen, presents five expert tips for cutting costs when designing custom CNC machined parts. This video covers corners and radii, designing for deep pockets, thread depths, thin walls, and more. Always excellent info from Paulsen at Xometry.
Make sure your parts meet expectations the first time around. Xometry's director of application engineering, Greg Paulsen, presents five expert tips for cutting costs when designing custom CNC machined parts. This video covers corners and radii, designing for deep pockets, thread depths, thin walls, and more. Always excellent info from Paulsen at Xometry.
View the video.
What can you secure with a retaining ring? 20 examples
 From the watch dial on your wrist to a wind turbine, no application is too small or too big for a Smalley retaining ring to secure. Light to heavy-duty loads? Carbon steel to exotic materials? No problem. See how retaining rings are used in slip clutches, bike locks, hip replacements, and even the Louvre Pyramid.
From the watch dial on your wrist to a wind turbine, no application is too small or too big for a Smalley retaining ring to secure. Light to heavy-duty loads? Carbon steel to exotic materials? No problem. See how retaining rings are used in slip clutches, bike locks, hip replacements, and even the Louvre Pyramid.
See the Smalley design applications.
Load fasteners with integrated RFID
 A crane, rope, or chain may be required when something needs lifting -- plus anchoring points on the load. JW Winco offers a wide range of solutions to fasten the load securely, including: lifting eye bolts and rings (with or without rotation), eye rings with ball bearings, threaded lifting pins, shackles, lifting points for welding, and more. Some, such as the GN 581 Safety Swivel Lifting Eye Bolts, even have integrated RFID tags to clearly identify specific lifting points during wear and safety inspections and manage them digitally and without system interruption.
A crane, rope, or chain may be required when something needs lifting -- plus anchoring points on the load. JW Winco offers a wide range of solutions to fasten the load securely, including: lifting eye bolts and rings (with or without rotation), eye rings with ball bearings, threaded lifting pins, shackles, lifting points for welding, and more. Some, such as the GN 581 Safety Swivel Lifting Eye Bolts, even have integrated RFID tags to clearly identify specific lifting points during wear and safety inspections and manage them digitally and without system interruption.
Learn more.
Couplings solve misalignments more precisely with targeted center designs
 ALS Couplings from Miki Pulley feature a simplistic, three-piece construction and are available in three different types for more precisely handling parallel, angular, or axial misalignment applications. The key feature of this coupling design is its center element. Each of the three models has a center member that has a unique and durable material and shape. Also called a "spider," the center is designed to address and resolve the type of misalignment targeted. Ideal for unidirectional continuous movement or rapid bidirectional motion.
ALS Couplings from Miki Pulley feature a simplistic, three-piece construction and are available in three different types for more precisely handling parallel, angular, or axial misalignment applications. The key feature of this coupling design is its center element. Each of the three models has a center member that has a unique and durable material and shape. Also called a "spider," the center is designed to address and resolve the type of misalignment targeted. Ideal for unidirectional continuous movement or rapid bidirectional motion.
Learn more.
What is 3D-MID? Molded parts with integrated electronics from HARTING
 3D-MID (three-dimensional mechatronic integrated devices) technology combines electronic and mechanical functionalities into a single, 3D component. It replaces the traditional printed circuit board and opens up many new opportunities. It takes injection-molded parts and uses laser-direct structuring to etch areas of conductor structures, which are filled with a copper plating process to create very precise electronic circuits. HARTING, the technology's developer, says it's "Like a PCB, but 3D." Tons of possibilities.
3D-MID (three-dimensional mechatronic integrated devices) technology combines electronic and mechanical functionalities into a single, 3D component. It replaces the traditional printed circuit board and opens up many new opportunities. It takes injection-molded parts and uses laser-direct structuring to etch areas of conductor structures, which are filled with a copper plating process to create very precise electronic circuits. HARTING, the technology's developer, says it's "Like a PCB, but 3D." Tons of possibilities.
View the video.
Novel transmitter protects wireless devices from hackers
Today, more than 8 billion devices are connected around the world, forming an "internet of things" that includes medical devices, wearables, vehicles, and smart household and city technologies. By 2020, experts estimate that number will rise to more than 20 billion devices, all uploading and sharing data online.
But those devices are vulnerable to hacker attacks that locate, intercept, and overwrite the data, jam signals, and generally wreak havoc. One method to protect the data is called "frequency hopping," which sends each data packet, containing thousands of individual bits, on a random, unique radio frequency (RF) channel, so hackers can't pin down any given packet. Hopping large packets, however, is just slow enough that hackers can still pull off an attack.
Now MIT researchers have developed a novel transmitter that frequency hops each individual 1 or 0 bit of a data packet, every microsecond, which is fast enough to thwart even the quickest hackers.
The transmitter leverages frequency-agile devices called bulk acoustic wave (BAW) resonators and rapidly switches between a wide range of RF channels, sending information for a data bit with each hop. In addition, the researchers incorporated a channel generator that, each microsecond, selects the random channel to send each bit. On top of that, the researchers developed a wireless protocol -- different from the protocol used today -- to support the ultrafast frequency hopping.
"With the current existing [transmitter] architecture, you wouldn't be able to hop data bits at that speed with low power," says Rabia Tugce Yazicigil, a postdoc in the Department of Electrical Engineering and Computer Science and first author on a paper describing the transmitter, which is being presented at the IEEE Radio Frequency Integrated Circuits Symposium. "By developing this protocol and radio frequency architecture together, we offer physical-layer security for connectivity of everything." Initially, this could mean securing smart meters that read home utilities, control heating, or monitor the grid.
"More seriously, perhaps, the transmitter could help secure medical devices, such as insulin pumps and pacemakers, that could be attacked if a hacker wants to harm someone," Yazicigil says. "When people start corrupting the messages [of these devices], it starts affecting people's lives."
Co-authors on the paper are Anantha P. Chandrakasan, dean of MIT's School of Engineering and the Vannevar Bush Professor of Electrical Engineering and Computer Science (EECS); former MIT postdoc Phillip Nadeau; former MIT undergraduate student Daniel Richman; EECS graduate student Chiraag Juvekar; and visiting research student Kapil Vaidya.
Ultrafast frequency hopping
One particularly sneaky attack on wireless devices is called selective jamming, where a hacker intercepts and corrupts data packets transmitting from a single device but leaves all other nearby devices unscathed. Such targeted attacks are difficult to identify, as they're often mistaken for poor a wireless link and are difficult to combat with current packet-level frequency-hopping transmitters.
With frequency hopping, a transmitter sends data on various channels, based on a predetermined sequence shared with the receiver. Packet-level frequency hopping sends one data packet at a time, on a single 1-megahertz channel, across a range of 80 channels. A packet takes around 612 microseconds for BLE-type transmitters to send on that channel. But attackers can locate the channel during the first 1 microsecond and then jam the packet.
"Because the packet stays in the channel for long time, and the attacker only needs a microsecond to identify the frequency, the attacker has enough time to overwrite the data in the remainder of the packet," Yazicigil says.
To build their ultrafast frequency-hopping method, the researchers first replaced a crystal oscillator -- which vibrates to create an electrical signal -- with an oscillator based on a BAW resonator. However, the BAW resonators only cover about 4 to 5 megahertz of frequency channels, falling far short of the 80-megahertz range available in the 2.4-gigahertz band designated for wireless communication. Continuing recent work on BAW resonators -- in a 2017 paper co-authored by Chandrakasan, Nadeau, and Yazicigil -- the researchers incorporated components that divide an input frequency into multiple frequencies. An additional mixer component combines the divided frequencies with the BAW's radio frequencies to create a host of new radio frequencies that can span about 80 channels.
Randomizing everything
The next step was randomizing how the data is sent. In traditional modulation schemes, when a transmitter sends data on a channel, that channel will display an offset -- a slight deviation in frequency. With BLE modulations, that offset is always a fixed 250 kilohertz for a 1 bit and a fixed -250 kilohertz for a 0 bit. A receiver simply notes the channel's 250-kilohertz or -250-kilohertz offset as each bit is sent and decodes the corresponding bits.
But that means, if hackers can pinpoint the carrier frequency, they too have access to that information. If hackers can see a 250-kilohertz offset on, say, channel 14, they'll know that's an incoming 1 and begin messing with the rest of the data packet.
To combat that, the researchers employed a system that each microsecond generates a pair of separate channels across the 80-channel spectrum. Based on a preshared secret key with the transmitter, the receiver does some calculations to designate one channel to carry a 1 bit and the other to carry a 0 bit. But the channel carrying the desired bit will always display more energy. The receiver then compares the energy in those two channels, notes which one has a higher energy, and decodes for the bit sent on that channel.
For example, by using the preshared key, the receiver will calculate that 1 will be sent on channel 14 and a 0 will be sent on channel 31 for one hop. But the transmitter only wants the receiver to decode a 1. The transmitter will send a 1 on channel 14, and send nothing on channel 31. The receiver sees channel 14 has a higher energy and, knowing that's a 1-bit channel, decodes a 1. In the next microsecond, the transmitter selects two more random channels for the next bit and repeats the process.
Because the channel selection is quick and random, and there is no fixed frequency offset, a hacker can never tell which bit is going to which channel. "For an attacker, that means they can't do any better than random guessing, making selective jamming infeasible," Yazicigil says.
As a final innovation, the researchers integrated two transmitter paths into a time-interleaved architecture. This allows the inactive transmitter to receive the selected next channel, while the active transmitter sends data on the current channel. Then, the workload alternates. Doing so ensures a 1-microsecond frequency-hop rate and, in turn, preserves the 1-megabyte-per-second data rate similar to BLE-type transmitters.
Source: Massachusetts Institute of Technology
Published June 2018
Rate this article
View our terms of use and privacy policy

